Hiring new employees is a critical function of doing business, and the onboarding process transcends industry, company size, and physical location. Organizations often need new talent to capture opportunity, optimize productivity, expand into new sectors, build products, and strengthen existing services. However, personnel transitions are equal opportunities for threat actors, and in some cases criminals, to exploit the hiring and onboarding process for the purposes of gaining unauthorized access to a valuable target. With new employees come new risks; from aspiring insider threats that intend to join a target to extract sensitive information, to insecure processes being exploited due to too much trust being placed in candidates and new hires.
It’s Never Too Early: Safeguarding the Interview Process
For today’s organizations, the reality is that the interview process has become a well-oiled machine. Companies set up profiles and job advertisements on job-search sites to elicit jobseekers to apply. Hiring managers field an influx of resumes and CVs and must decide who they will hire.
During this process, potential candidates are often required to speak to executives, managers, and team members associated with the position of interest. Who has not been to a job interview where a current employee overshares plans, capabilities, frustrations, or financial outlook? For a criminal threat actor who is an adept social engineer, a job interview is a golden opportunity to extract sensitive information about the target, its employees, and other valuable information. This can be particularly useful information for cyber criminals who may leverage the details in phishing or vishing campaigns to get one step closer to the organization’s crown jewels.
Often, hiring managers and team members are not considering security when interviewing prospective new employees. It would be a rare occurrence that interviewers were trained or even reminded of security concerns during the interview and vetting process. The results are self-evident and, without reminders, employees may overshare without even knowing it. Planning to protect your business and its property should include actions to defend all possible vectors during the vetting and interviewing processes. Defense shouldn’t stop there, however, since the onboarding process is another transition criminals can exploit.
Welcome to the Team! Please Meet Our Security Protocol
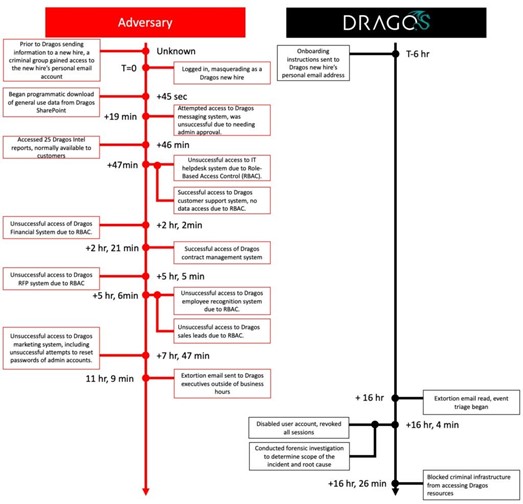
The transition from prospective candidate to full-time employee can include an onboarding process, where the oncoming employee completes a number of steps to be a part of the team. This procedure almost always starts with an email sent to the new hire’s personal email address. Just this action shifts a lot of risk from the corporate security posture over to the new employee. If, for example, the new employee’s personal email account was compromised, an attacker can insert themselves into the onboarding process. This vector grabbed the attention of the information security community recently when the cybersecurity firm Dragos was exploited in this manner. In Dragos’ situation, the threat actor breached the personal email inbox of a newly hired sales staff member. As seen in the attack timeline published by Dragos (Figure 1), the attacker attempted to access various resources in Dragos’ internal infrastructure, deploy ransomware, and extort executives at the company. Thankfully, due to security measures put in place at the company, the actor’s attempts were unsuccessful.
Figure 1: Dragos Breach Timeline (Source: Dragos)
Dragos’ approach of reporting quickly and with great detail should be applauded. They have provided a venue to have a public discussion about risks in the onboarding process, and the community will benefit from the many lessons to be learned from their disclosure.
As a general lesson, new hires should not be provisioned full privileges akin to those given to longtime trusted employees. It is common for new hires to acquire broad access into the employer’s key information through shared storage devices, cloud-based assets, and other locations with data well beyond the scope of the employee’s role in the organization. Limiting the new employee’s access to only data needed to perform the assigned role is key to mitigating the potential damage from an information leak, whether intentional, or not.
All accounts, especially for new hires, should be set up with multi-factor authentication (MFA) to deny attackers from using previously breached credentials (usernames and passwords) and to defend the new employer from employee password reuse. From the outset, user behavior analytics (UBA) processes are a good way to defend against anomalies in the onboarding process. An example of this is when an employee starts their onboarding process in the United States from an IP address confirmed to be associated with their internet service provider (ISP), the process should proceed as normal. Any aberrations to that validated baseline should be detected and adjudicated. Connections from an unknown virtual private network (VPN) service or cloud hosting provider should be detected and denied unless validated verbally by the new employee.
Remote and Hybrid Work Add Complexity
Traditional cybersecurity incidents are not the only threat employers face when hiring a new employee. With the move to remote and hybrid work, it is possible that the new hire is not always who they seem to be.
Communities of workers have been observed presenting themselves as being dedicated to only one company when they hold multiple remote jobs that they balance throughout the day. Unscrupulous entrepreneurs have created illegitimate contracting companies that “subcontract” their multiple jobs to teams of workers in lower wage countries, such as India and China. The employee then acts as an intermediary translating the work given to them by their workers to the unsuspecting employer, representing it as their own.
Notably, North Korea has taken advantage of the cover offered by remote work and is duping unsuspecting companies through misrepresentation. The U.S. Departments of State and Treasury and the Federal Bureau of Investigations (FBI) released a warning in May 2022 that the Democratic People’s Republic of Korea (DPRK) has dispatched “thousands” of freelance workers in the information technology field to generate revenue for the government. This revenue then directly contributes to funding programs to strengthen their military capabilities. Businesses employing these workers may then be liable for breaching U.S. and United Nations (UN) sanctions. While they mainly conduct non-malicious IT work, these DPRK workers have also been providing support malicious cyber operations when they have the opportunity. While North Korean freelancers or employees are hopefully few and far between, risks that are much more prevalent include those that come with the new employees and their devices.
Bring Your Own Device = Businesses Own Employee Risks
The Bring Your Own Device (BYOD) solution to productivity and the enabling policies allowing BYOD, have become more prevalent in the business infrastructure today. In fact, most workers believe their own devices are more efficient and productive than those given to them by their workplace. Though there may be advantages to BYOD policies, a poorly implemented BYOD program introduces increased risk.
Effective BYOD programs must maintain strong security precautions such as endpoint detection and data loss prevention solutions. If an employee decided to use their personal device to exfiltrate valuable corporate information, without proper safeguards, there is often little to no trace of that action after the fact. In addition, if an employee is not careful on the Internet, they could download malware and without endpoint detection and response, exploitation could soon follow. Physical attacks are also an issue for BYOD related infrastructure. If an employee’s device is lost or stolen, it is unlikely an employer could remotely lock or securely wipe the system without some business-owned solution on the device and the user’s consent to enable that action.
Finding the Right Balance: Protection and Culture of Trust
Companies faced with the various risks of hiring and onboarding should be careful not to overreach and should strike a balance between security and operability. For example, we have seen companies require all potential job candidates to sign a Non-Disclosure Agreement (NDA) before beginning substantial interviews and salary negotiations. NDAs this early in the relationship however can send the message that the company has a strict working environment and generally distrusts employees. When security practices trample on relationships and trust building, those practices are likely ignored when it matters most. For example, organizations may believe they are covered by asking a candidate to sign an NDA at reception upon arriving for an in-person interview; however, a receptionist who is not trained in legal protocol may not realize that a candidate signed the documentation with a fake name. Additionally, asking for an NDA at the beginning of the relationship with the candidate could feel overly intrusive and sour the candidate’s opinion on the organization’s core values or cause them to drop out altogether. While some high-stakes roles may require mutual discretion, an NDA may not be appropriate for all.
A better approach is to plan beforehand to protect information by discussing expectations with those involved in conducting candidate screenings, interviews, salary negotiations, and onboarding, by controlling variables and risk directly with those already in the organization itself. Protection programs should come into play before the employee is hired as recruiters and hiring managers should perform basic vetting to confirm the candidate is who they say they are. Initial protection measures could be as simple as asking candidates to show their ID while on camera to confirm it matches the person presenting it. Particularly if jobs are remote or hybrid, organizations can consider confirming the physical location where the candidate will be routinely connecting from during the process and noting that location in case anomalies are detected. While potentially unconventional, recent lessons learned from Dragos’ latest event and other issues suggest measures such as these are now needed. Protection programs should include regular awareness messages from leaders, periodic training about how to defend key company information, and follow-up discussions with new employees about their hiring and onboarding experiences.
Bringing new team members into the fold is an exciting time for most companies. However, the hiring and onboarding process can include tangible risks to information, personnel, and reputation. Plan to protect your business interests now, before the hiring action starts. Confirm interview and hiring procedures include information defense and infrastructure protection strategies that weigh risks in a meaningful way. Instruct, train, and follow up with those who interact with candidates to ensure valuable information is not inadvertently leaking and that your cybersecurity posture doesn’t suffer during the hiring process. Failure to do so can yield dire consequences before Day One.
Reprinted with permission from the June 2023 issue of Cybersecurity Law & Strategy. © 2023 ALM Media Properties, LLC. Further duplication without permission is prohibited. All rights reserved.