The phenomenon of North Korean (DPRK) IT workers successfully gaining employment with organizations in the U.S. and other western countries has been big news in recent months. The unique national security and geopolitical considerations connected to North Korea add to the story’s intrigue, but at its heart, this is simply one of many forms of Insider Threat businesses must defend against on a daily basis.
What is Happening?
Operatives based in the DPRK leverage stolen or fabricated identities to apply for jobs in U.S. entities. To conceal their actual identities and location, they utilize Virtual Private Networks (VPNs), which obfuscate and misrepresent their actual location. They avoid in-person calls and sometimes use AI countermeasures to circumvent the interview and hiring process.
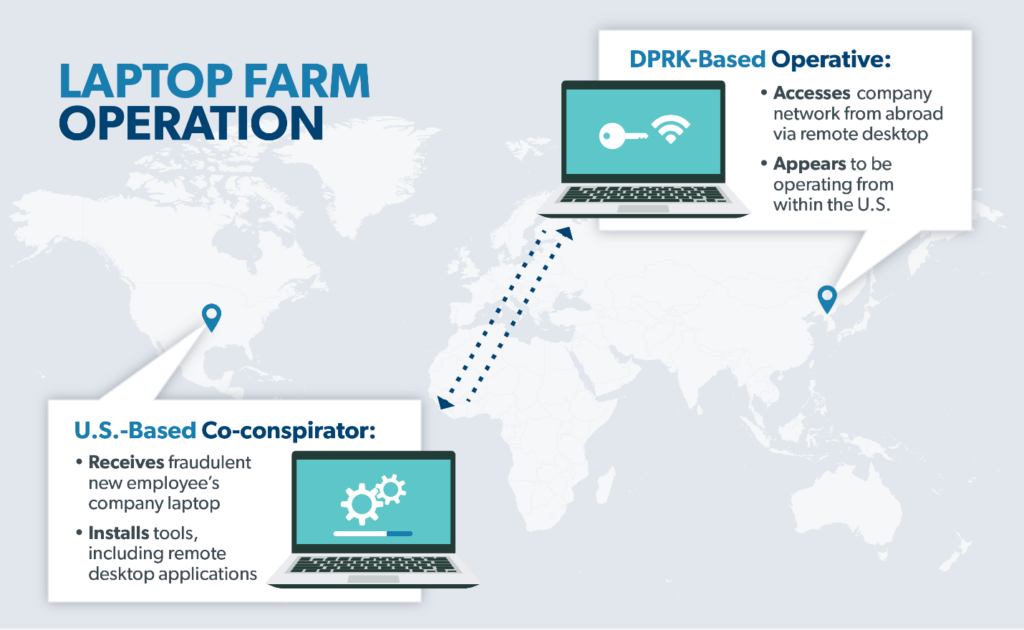
U.S. authorities have also discovered a network of U.S.-based co-conspirators supporting these schemes in various ways, including the use of U.S.-based “laptop farms” in which U.S.-based operatives receive the fraudulent new employee’s company devices and install tools, including remote desktop applications, that enable the DPRK-based operative to access the company network from abroad and appear as if they are in fact located in the U.S.
The Threats
By unwittingly hiring these fraudsters, companies open themselves up to numerous risks, such as:
Cyber Compromise
Having obtained approved access to company systems masquerading as a legitimate employee, the threat actors may be able to obtain unauthorized access to other systems, exfiltrate data (including intellectual property and sensitive financial, customer, and/or personnel data), deploy malware or further compromise networks, or launch a ransomware attack to extort the victim company.
Financial Support to Foreign Enemies
Many fraudulent DPRK employees behave as diligent employees to maintain continued employment, thus generating income and revenue that is funneled back the DPRK, where those funds may be used to support the DPRK economy or strategic priorities, including military and weapons programs, or further expand cybercrime resources.
Legal Concerns
The DPRK is a heavily sanctioned and restricted nation. In fact, the U.S. Treasury Department’s Office of Foreign Assets Control (OFAC) restricts the employment of DPRK nationals. These bad actors may be obtaining proprietary information or export controlled/restricted items and sending them back to the DPRK. Companies with DPRK operatives in their employment may unintentionally run afoul of many legal or regulatory requirements. Under OFAC, victim companies may be found liable for sanctions violations or other regulatory action, regardless of their knowledge or intent!
Protect Yourself
A well-developed security program will include controls specifically designed to look for and defend against Insider Threats. Because of the diverse techniques these threat actors employ, multiple techniques may help provide good indicators to identify a potential DPRKIT worker.
Physical Address Irregularities
Be on the lookout for address information changing, unusual recipients for corporate devices (e.g., individual with no relation to the new employee), or use of mail forwarding services. Since these actors are not U.S. based, they often need to rely on some domestic infrastructure or support services to successfully gain access to corporate issued devices.
Remote Management Tools
Since threat actors are trying to obfuscate their true location, look for the installation of Keyboard Video Mouse (KVM) tools to newly provisioned endpoints (e.g., TeamViewer, Chrome Remote Desktop, LogMeIn, AnyDesk, RustDesk, etc.). This should warrant closer scrutiny, especially if these tools are not approved or used at the enterprise level or if multiple tools are installed on the same device.
Suspicious Payment Methods
As described, one objective for DPRK IT workers can be receiving compensation for their services to support North Korean priorities. As such, keep an eye out for new employees asking for payment via cryptocurrency or using newer internet banking services. Without being in the United States, they are more likely to use services which have less rigorous Know Your Customer (KYC) processes.
Productivity Anomalies
As these threat actors often want to access sensitive information to exfiltrate it, look out for work occurring during unusual hours or attempts to access files beyond the scope of their role or responsibilities.
In-Person Onboarding
While not feasible in all instances because of remote work arrangements, in-person training and onboarding could serve as effective methods for detecting or deterring DPRK IT workers. These protocols could be implemented as a standard practice or as an enhanced security measure when certain red flags are identified.
Conclusion
As threat actors evolve, organizations need to keep pace by developing multi-layered detection and mitigation strategies. Ongoing evaluation and refinement of these controls, amidst a constantly changing threat landscape, will only work to reinforce the strength of security programs.
If you have any questions or would like to discuss these topics please reach out to Nathan Fisher or Martin Narciso.
To receive StoneTurn Insights, sign up for our newsletter.