This article builds on “Tariffs Meet COSO: A Two-Way Street to Risk & Opportunity Management,” which introduces the COSO Integrated Internal Control Framework and explains how to use it to meet tariff operations, reporting and compliance objectives. Here, we present a 10-step process for using COSO’s risk assessment component to avoid tariff under- and overpayments, mitigate legal and reputational harm and identify potential opportunities for operational efficiencies.
1. Start with Clear, Measurable Objectives.
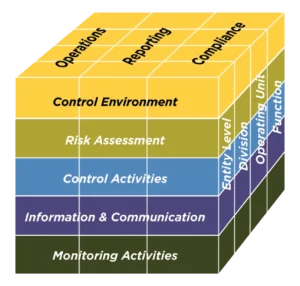
As discussed in the COSO article, the framework is commonly depicted as a cube. The top side of the cube refers to the objectives the organization seeks to achieve. Risks are events and scenarios that prevent companies from achieving objectives. Conversely, opportunities are events and scenarios that help achieve objectives.
Tariffs implicate all three objectives listed in the cube’s top side.
- Operational Objectives focus on financial goals and efficiency in day-to-day operations.
- Reporting Objectives include financial and non-financial reporting (e.g., accounting implications, the Harmonized Tariff Schedule (HTS) classification, valuation, country of origin, other customs documentation).
- Compliance Objectives refer to adherence with tariff legal, regulatory and other requirements.
2. Frame Risks and Opportunities as Events and Scenarios.
Risks and opportunities are potential events and scenarios that impede or facilitate companies from meeting their operational, reporting, and compliance objectives. Legal citations are not helpful. Nor are broad descriptions without accompanying schemes and scenarios. For example, misrepresentation of the country of origin is a risk. Still, it is not helpful without describing the schemes and scenarios through which misrepresentation may occur (e.g., transshipment through third countries, falsified or altered certificates of origin, minor processing in a low-tariff country, commingling goods from multiple origins). We recommend adopting a consistent format that describes the cause, scenario, and impact.
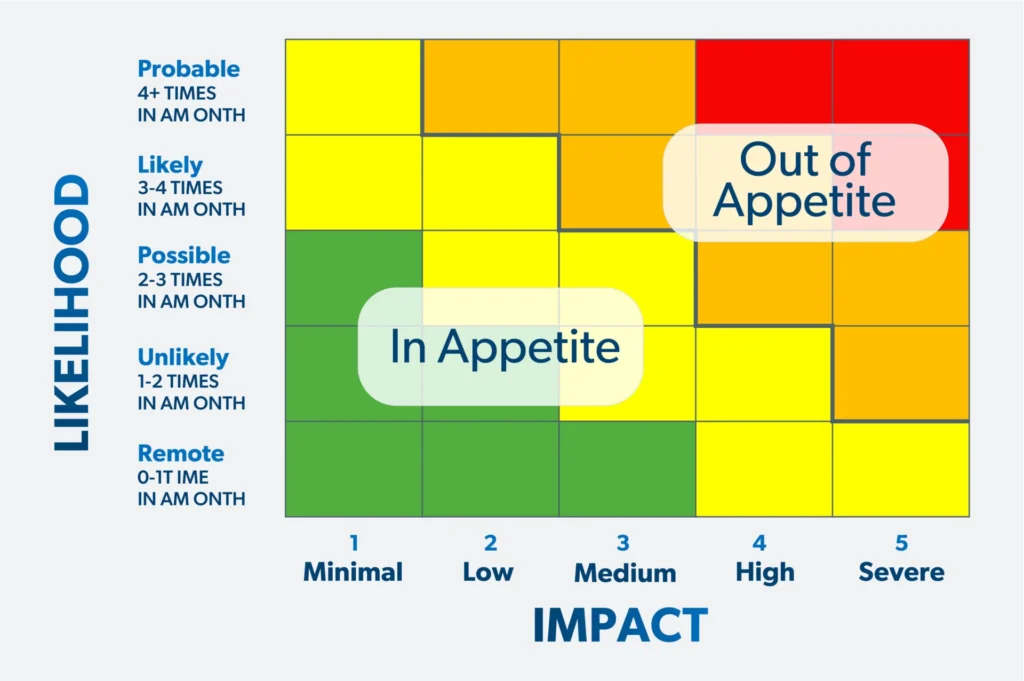
3. Set Risk Appetite and Tolerance.
Risk appetite refers to the level of risk an organization is willing to take on. Risk tolerance is the highest level of risk the organization can handle before it becomes unacceptable. Appetite is the range; tolerance is the absolute limit.
Think of it like a thermostat. Risk appetite is your comfort zone, while risk tolerance marks the point where action is unavoidable. This distinction matters because organizations operating within their risk appetite can take on more risk, as long as it remains within their risk tolerance.
Map risk appetite and tolerance across two axes: the probability of the tariff-related event or scenario occurring and the business, reputational, and legal impact if it materializes.
4. Inventory Laws and Regulations.
Compliance presumably is one of the objectives. Given the rapidly changing environment, companies should consult with internal or external counsel to establish a process for developing and maintaining an inventory of tariff-related laws, regulations, and other requirements.
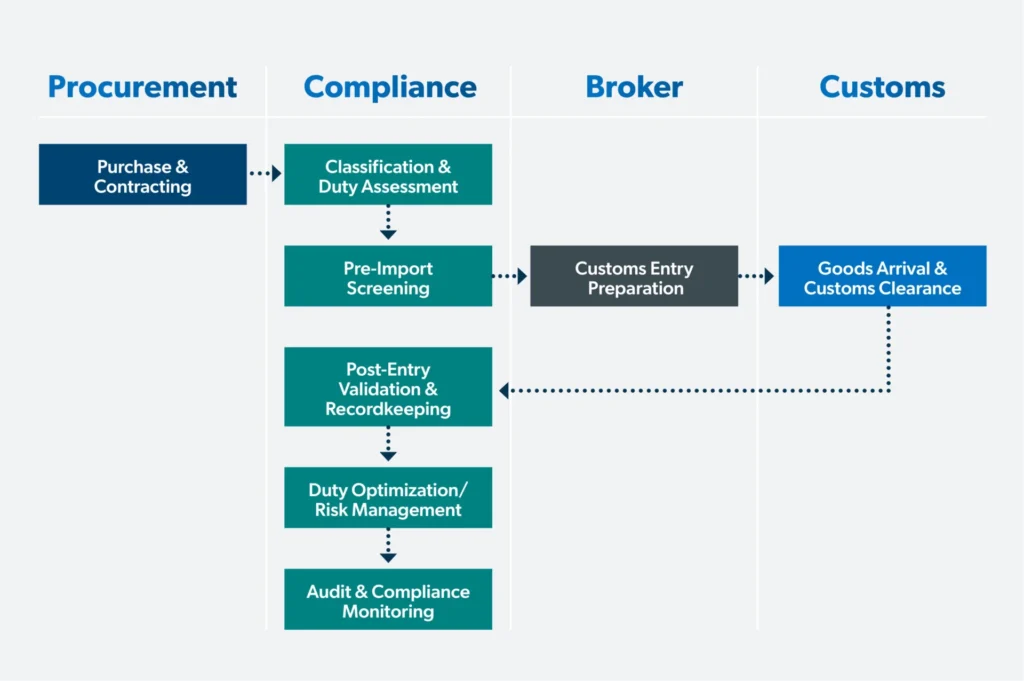
5. Map Tariff-Related Process Flows.
Tariffs involve various business functions (e.g., compliance, procurement, finance) and processes (e.g., HTS classification, customs valuation, country of origin determination, free trade agreement and preference program management, broker and entry management, supply). Working with the functions, create detailed process flows. Like the Laws and Regulations Inventory, utilize the process flows to identify “what can go wrong” and “what can go right” at each step in the process.
6. Identify Inherent Tariff Risks and Opportunities.
Inherent risk assesses the likelihood and impact without regard to mitigating policies, processes, and controls (collectively, “controls”) from internal and external sources. The most effective results are achieved through cross-functional brainstorming, which brings together compliance, operations, finance, and procurement teams in one to two-hour facilitated workshops.
Organizations should consider kicking off with icebreakers to help participants think like fraudsters and warn them about the risks of the “it won’t happen here” optimism bias. For example, we often start with an “Angels v. Demons” game, pitting one side against the other to determine how to commit or prevent a scheme from occurring.
- List Potential Scenarios. Begin by brainstorming potential events and scenarios from each step in the process diagram. Don’t be concerned about the likelihood or impact. Perform the same exercise for each of the laws and regulations in the inventory. Other sources include prior violations, past risk assessments, self-identified issues, audit findings, industry knowledge, case law, databases, and AI prompts.
- Assess Likelihood and Impact. Apply company standards for assessing likelihood and impact. For example, some companies assess likelihood based on the probability of the risk occurring within a year. Other companies measure likelihood based on the anticipated number of occurrences over the next one, three, five, or ten years. Some companies multiply probability and impact to derive a single score. Other companies assess likelihood and impact separately. There is no single correct way, but the approach must be statistically valid, well-documented, and defensible.
- Within Appetite Inherent Risks. Companies can de-prioritize events and schemes that fall within their risk appetite for compliance risk. Don’t lose sight, however, of opportunities to cut costs. For example, what controls has your company or client implemented to address inherent risks that fall within risk appetite? Can the company cut costs and increase efficiency by eliminating or reducing these controls? And what about inherent risks that fall within its appetite but below risk tolerance? Can your company or client accept greater risk? When assessing, consider the robustness of the risk assessment process and your dependency on accurate risk rating results.
7. Link Risks to Key Control Activities.
This and the following steps apply only to out-of-appetite inherent risks.
Control activities refer to the policies, processes, and controls (collectively, “controls”) that the company relies on to mitigate risks and maximize opportunities. These topics warrant a separate installment.
At this juncture, we emphasize the importance of identifying key controls. Companies tend to accumulate controls like many of us accumulate “stuff” in our personal lives. Focusing on key controls provides an opportunity for companies to eliminate or reduce unnecessary or redundant controls.
It is also essential to consider the control suite,¹ not just individual controls. Auditors tend to test whether controls meet the control objectives. Here, the question is whether the control suite brings inherent risks within its risk appetite.
8. Avoid Overreliance on Untested Controls.
Risks and controls experts differentiate between design and operating effectiveness. Design effectiveness assesses whether the controls operating as designed would mitigate the risk within the established risk appetite. It is imperative to evaluate vulnerability to collusion, management override, or other circumvention. Operating effectiveness tests the controls as executed in practice, including the competency and authority of personnel responsible for executing the controls.
As a practical matter, many companies will not have had an opportunity to test tariff controls’ design and operating effectiveness before conducting the risk and opportunity assessment. For example, past assessments may have deemed tariffs low-risk, or the company may have just recently implemented the controls.
Overreliance on untested controls is a risk unto itself. The risk assessment should denote that the control suite has not been tested and arrange for testing during the next compliance or internal audit testing cycle.
9. Select a Response to Out-of-Appetite Residual Risks.
Residual risk takes controls into account. The first step is to prioritize among multiple out-of-appetite residual risks. Factors to consider include the companies’ ability to adapt and respond to risks, the risk’s impact on the company’s success, and the speed at which the risk, if it materializes, affects the company. Companies may prioritize certain out-of-appetite risks that worsen rapidly if not addressed (e.g., deliberate misrepresentation of country of origin), or there may be the ability to have quick wins with relatively low investment to reduce the risk exposure, while other risks may require long-term remediation efforts.
Classic risk responses are: (1) accept the risk (e.g., disregard whether a vendor might misstate place of origin); (2) avoid the risk (e.g., restructuring business model to avoid tariffs); (3) share the risk (e.g., requiring suppliers to certify country of origin and trade documentation); and (4) reduce the risk, by, for example, implementing preventive and detective controls (e.g., contractual safeguards with suppliers and duty variance analysis).
Creating a risk reduction strategy is similar to developing a remediation plan. Begin by understanding the rationale of the residual risk through a root cause analysis. Next, identify possible risk reduction methods, including implementing preventive and detective controls, and leveraging the Fraud Triangle to reduce incentives, pressure, and rationalization.
10. Stick to the Risk Response Plan.
Lawyers and compliance officers sometimes disagree on whether to document the risk assessment. Some lawyers believe that documenting risks exposes the company if the risk materializes. The counter-argument is that a documented risk response demonstrates a good-faith effort to mitigate risk. Either way, adhering to the plan and maintaining evidence of the organization’s efforts is crucial.
* * *
Effective risk assessment can be the difference between predictable margins and costly disruptions in today’s high-stakes environment, where enforcement scrutiny is increasing and tariff rules are shifting rapidly. COSO’s structured approach ensures that inherent and residual risks are identified, measured, prioritized, and addressed in line with the company’s appetite and tolerance. Just as importantly, it uncovers opportunities to streamline controls and capture legitimate tariff savings. Disciplined risk assessment transforms tariffs from a compliance burden into a strategic tool for enhancing performance and resilience.
¹A control suite is a set or grouping of control activities, including the culture, governance and entity-level policies, to meet objectives, mitigate risks, and maximize opportunities.
Ready to strengthen your tariff management strategy and reduce risks? Reach out to Jonny Frank or Laura Greenman for expert guidance on navigating the complexities of tariffs in your business.
To receive StoneTurn Insights, sign up for our newsletter.